Modern cyberattacks are often designed to catch victims off guard. One way they do this is by hiding malicious software and other threats in plain sight. If not handled properly, this malware can infect a computer system and cause significant damage or steal sensitive information. Let’s consider these five common scenarios that can lead to a malware infection on your computer.
1. Email Attachments
Emails remain the most common way of infecting computers. Criminals use social engineering to trick victims into opening links with malicious content and downloading attachments that contain malware.
Attachments can come in many forms, including PDFs, Word documents, and executable files. After running or opening these files, the infection chain will begin, allowing the malware to establish its presence on the system and begin its activities.
One of the most effective ways to protect against this type of attack is to use a malware sandbox. Services like ANY.RUN let you upload your emails, attachments, and links to it right in your browser and analyze them. The sandbox reveals all the details about the malware or threats found in the samples you provide, giving you a conclusive verdict on whether they are safe.
Take a look at this sandbox session where we analyze an email in the .eml format.
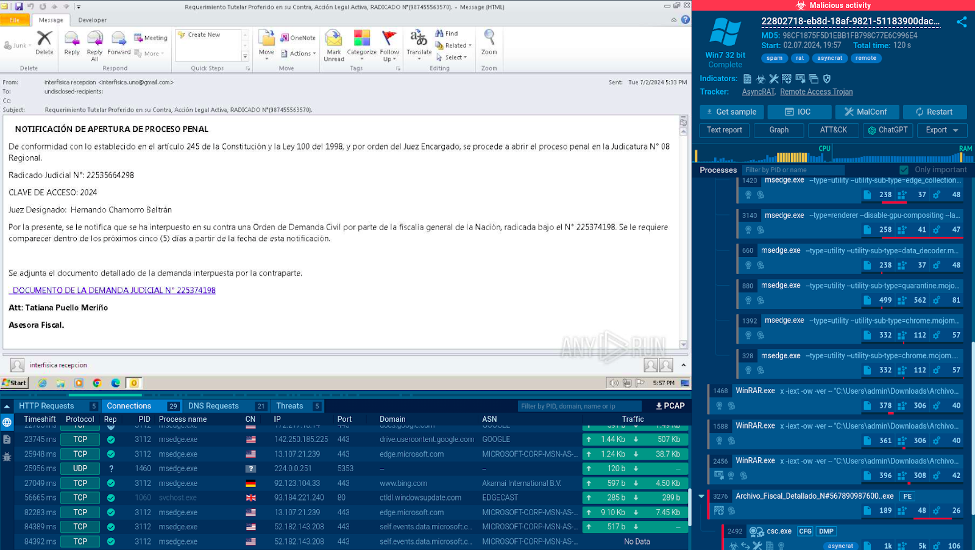
The sandbox lets us open the email and navigate to the link it contains. The link takes us to a page where we are offered to download an archive.
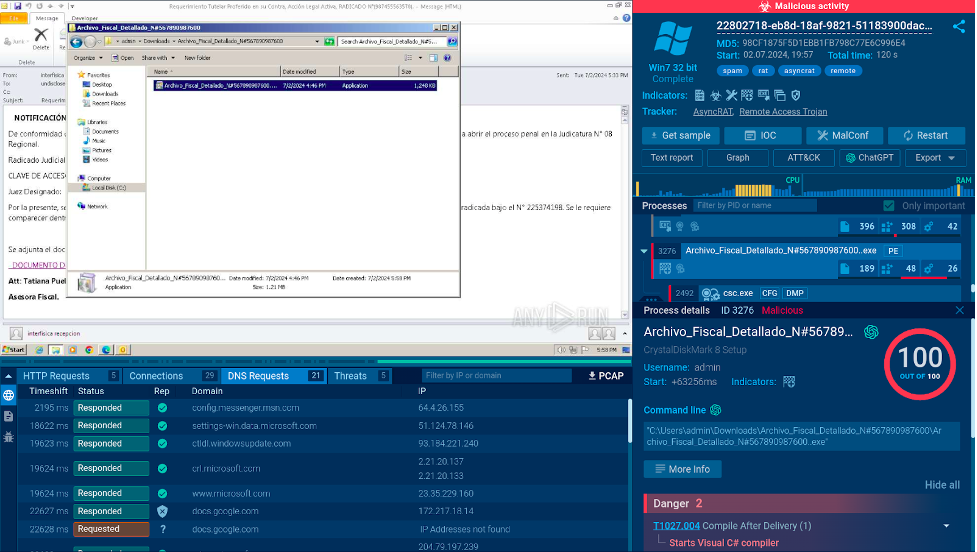
After downloading the archive inside the sandbox, we open it and discover an executable file. Once we run it, the sandbox immediately identifies the presence of AsyncRAT, a common malware family that is used by criminals to control infected computers.
2. Infected Software Downloads
Another common scenario that can lead to a malware infection is downloading infected software. Cybercriminals often use legitimate-looking websites to distribute malware disguised as popular software programs. When users download and install these programs, they unknowingly install malware on their computers.
For example, here is a sandbox session featuring an analysis of an .exe file named “OneDrive”, a popular Microsoft software.
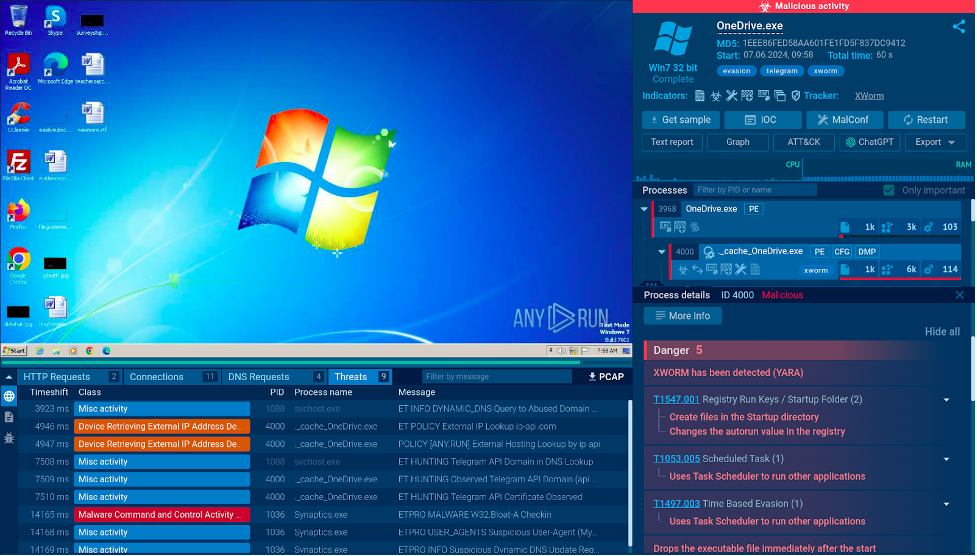
Once executed in the sandbox, we can instantly see that it is a malware, specifically the XWorm RAT, which can steal sensitive information from the infected machine.
To avoid falling victim to this type of attack, it is crucial to only download software from trusted sources, such as the official website of the software vendor.
3. Malicious Advertisements
Malicious advertisements, also known as malvertising, is another threat that can lead to an infection.
Cybercriminals can abuse legitimate services like Google Ads to promote their websites, where users can be tricked into downloading and then running malware on their computers.
One of the recent malvertising attacks involving the distribution of the MadMxShell backdoor masked as the legitimate software Advanced IP Scanner.
Below, you can observe an analysis of a sample of this malware.
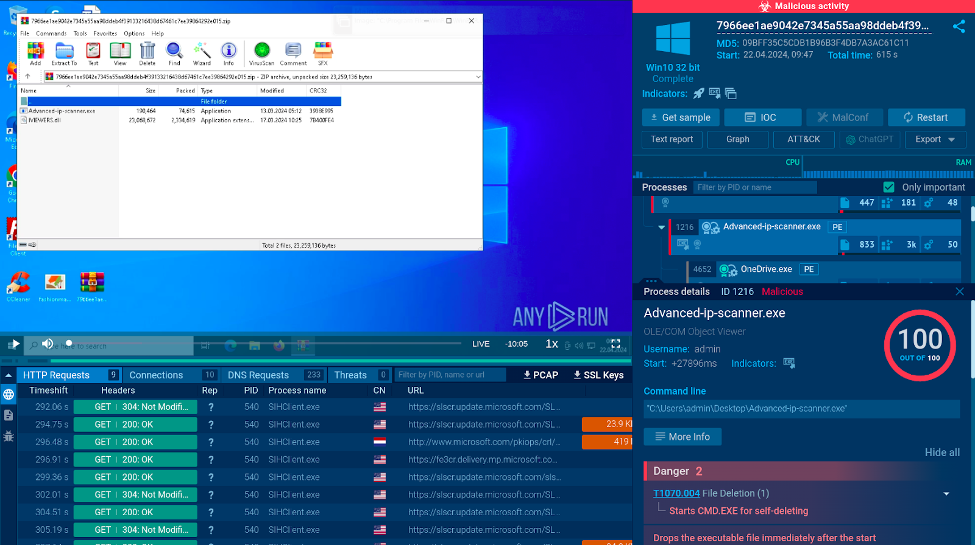
As in the example above, the malware itself is hidden inside an archive, which is commonly used to evade detection by antivirus solutions.
To protect yourself from malvertising, it is essential to keep your web browser and security software up to date. Additionally, consider using an ad blocker to help prevent malicious advertisements from being displayed in the first place.
4. Unpatched Software Vulnerabilities
Software vulnerabilities are flaws in software programs that can be exploited by cybercriminals to gain unauthorized access to a computer system. If left unpatched, these vulnerabilities can provide an easy entry point for malware.
One example of such a flaw is CVE-2022-30190. This vulnerability, despite being discovered and subsequently patched in 2022, is still exploited by attackers on systems which did not receive any update.
In the session below, we can observe how this vulnerability is used in a .doc file. By opening this document in Word, the user allows the criminals to gain elevated privileges and execute any code remotely.
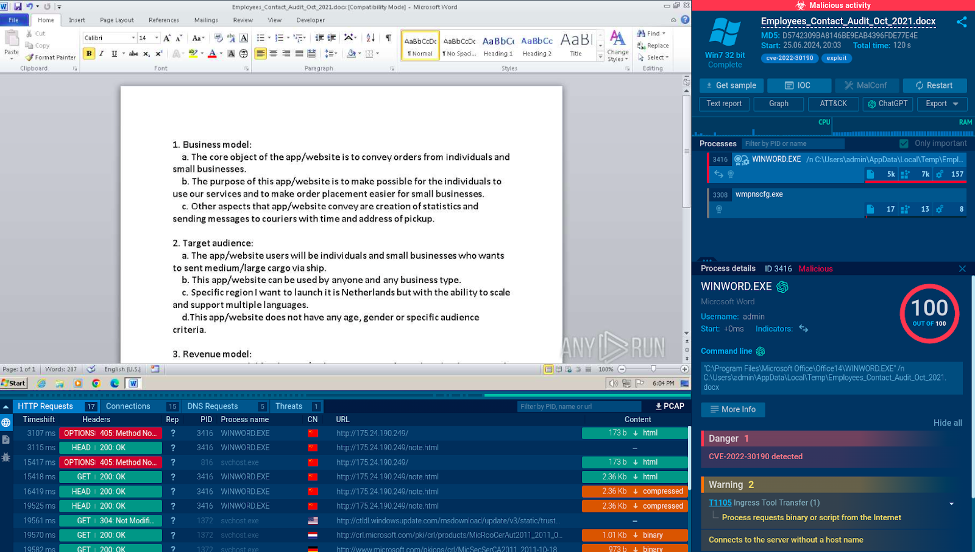
To prevent this type of attack, it is crucial to keep all software programs up to date with the latest security patches.
5. Infected Removable Media
Finally, infected removable media, such as USB drives and external hard drives, can also lead to a malware infection. Cybercriminals can infect these devices with malware and then distribute them to unsuspecting users. Once inserted into a computer, the malware can install itself and begin to cause damage.
Raspberry Robin is an example of a malware family that spreads across systems using removable drives. It has been particularly active since the start of 2024.
This sandbox analysis shows us how it operates.
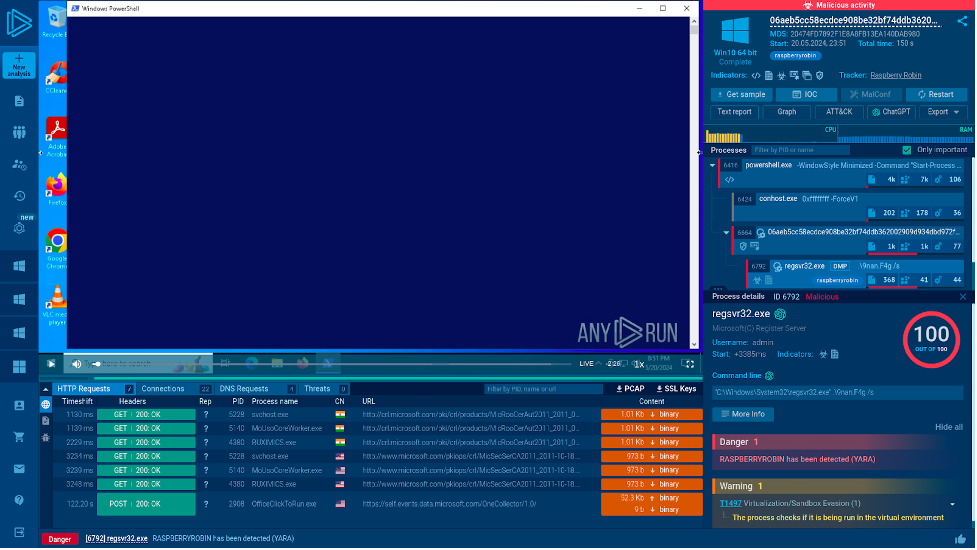
The malware gets executed via PowerShell and once it gains persistence on the machine, it connects to its command-and-control server, requesting additional instructions. Most often, it then downloads other malware, such as ransomware that encrypts files on the system and demands a ransom.
To protect yourself from this type of attack, it is essential to be cautious when using removable media, especially if it comes from an unknown source. Always scan removable media with antivirus software before using it on your computer.
Conclusion
By opening email attachments, downloaded software, and exploring suspicious links in a sandbox, you can prevent malware infection on your own device. Always remember to keep your systems up to date and consider using additional security tools, such as a vulnerability scanner and ad blocker, to help further protect your computer from malware.

